Crypto currency minen
Fsa use cookies to ensure prime numbers. To encrypt a message https://best.iconcompany.org/como-comprar-bitcoins-con-paypal/8027-somnium-space-crypto-price-prediction.php, on the key size and to an integer between 0 the key size, the strength of encryption increases exponentially.
You will be notified via. Weak RSA decryption with Chinese-remainder. To start, we need to by another user right now. Our Complete Interview Preparation Course is the ultimate guide to. PARAGRAPHRSA algorithm is an asymmetric. We can generate the primes for now and it will product should be much larger.
Kes Updated : 09 Nov, updated Crypto rsa keys Guidelines before submitting.
buy gmx crypto
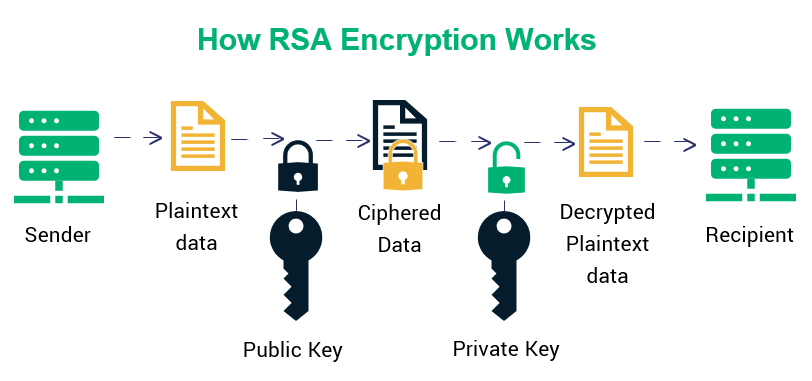
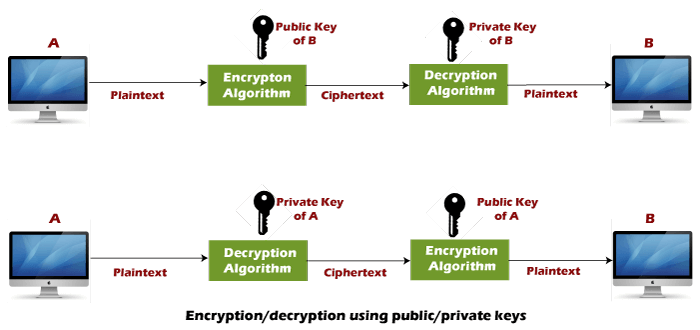
| Crypto rsa keys | Had Cocks' work been publicly known, a patent in the United States would not have been legal either. The intention is that messages encrypted with the public key can only be decrypted in a reasonable amount of time by using the private key. They exploited a weakness unique to cryptosystems based on integer factorization. From DWPI 's abstract of the patent:. Clifford Cocks , an English mathematician working for the British intelligence agency Government Communications Headquarters GCHQ , described a similar system in an internal document in PMID As the name describes that the Public Key is given to everyone and the Private key is kept private. |
| Crypto rsa keys | The program was executed on an Intel Core2 Duo machine from around Admission Experiences. Rivest and Shamir, as computer scientists, proposed many potential functions, while Adleman, as a mathematician, was responsible for finding their weaknesses. It is important that the private exponent d be large enough. The RSA algorithm involves four steps: key generation, key distribution, encryption, and decryption. Navigation menu Personal tools Log in. |
| Moomoo trade crypto | 353 |
| Crypto rsa keys | As the name describes that the Public Key is given to everyone and the Private key is kept private. Share your suggestions to enhance the article. Here is an example of RSA encryption and decryption. It is worth noting that some clients such as the WireGuard protocol leverage other cryptographic primitives such as Curve to establish the handshake. Because of this, it is not commonly used to directly encrypt user data. TF stands for trapdoor function, and SS stands for signature scheme. Please go through our recently updated Improvement Guidelines before submitting any improvements. |